Penetration Testing Microsoft Exchange
Authored by: Raul M.
Topics
Email Server Identification
Exchange Version Enumeration
User enumeration
SMTP Relay
Intro
Like any penetration test it must begin with some target identification and enumeration, oh and most importantly scope confirmation! After confirming with the client, we find out we need to focus on a single host (10.0.0.6). Since we don’t know much about the environment and have a single host in scope, we can ask a few follow-up questions to ensure we don’t break things:
Is it a windows environment? Yes
Is there a domain controller? Yes
What’s the domain? corp.kkms.local
What’s the lockout policy? I’m not sure
Are there any domains we should avoid? No
Target Enumeration
I think the simplest tool for target enumeration is nmap. Nmap is a network mapping tool that lets you find ports and services offered by various network devices. Let's start off by building the command. We know we want to find the ports and services, but which do we care about? Do we want to scan all ports and services, or maybe we want to find specific services? In our case we will be performing a TCP service versioning (-sV) scan on all the TCP ports (-p-):
After reviewing the output of the scan, I think it's reasonably safe to assume that this is an exchange server But which version? In the results we see “Microsoft Exchange 2007-2010" all over the place. While helpful, this really is a wide net we are casting. We need to gather some other information before we continue with our testing.
Exchange Version Enumeration
To get the Exchange version we need to understand what the services we found do. The diagram below shows a subset of the ports we found were “open”, but we’ll specifically focus on the Exchange Web Services (EWS). EWS supplies programmatic access to the exchange backend. In our current state we do not have credentials, so we’ll only be using EWS to find the Exchange version.
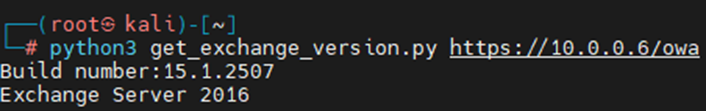
Fortunately, there is a script written by ’kh4sh3i’ on GitHub, that automagically makes a request to EWS and prints out the build and exchange version:
In this case we find we are targeting Exchange 2016 build 15.1.2507. We can now use the build number to find various vulnerabilities that may or may not exist.
User Enumeration
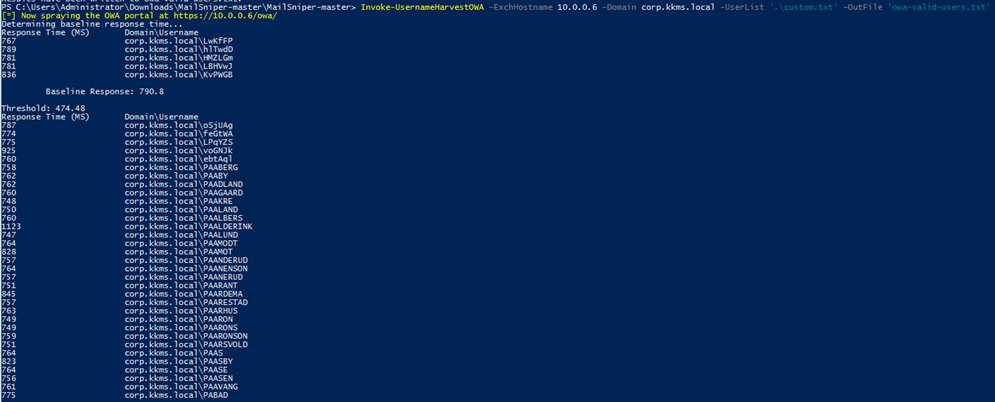
Like version enumeration, user enumeration is just as easy with the right tools. MailSniper another open source tool available on GitHub, makes it super easy to perform various tasks against an exchange server. Because MailSniper is a PowerShell tool we’ll need to move over to a windows box and open PowerShell. Once we have PowerShell open, we can import the mailsniper module and use the “Invoke-UsernameHarvestOWA” cmdlet. This will allow us to perform a timing attack to find any potentially valid usernames.
Once we find a valid user, we can move to finding any vulnerabilities with the SMTP Protocol.
SMTP Relay
In some organizations you’ll find that an SMTP server is not always configured with the proper security controls. From my experience this is typically because there is a device somewhere on the network that cannot perform authenticated SMTP requests and requires the server to be configured to accept unauthenticated SMTP requests. Because this is a penetration test and not a red team engagement, we need to talk to the client and let them know what has been found and the testing we want to perform. Some clients will give you free reign to test however you’d like but some may want something more controlled. In this case, we will do something more controlled, but note that we must talk to the client first!
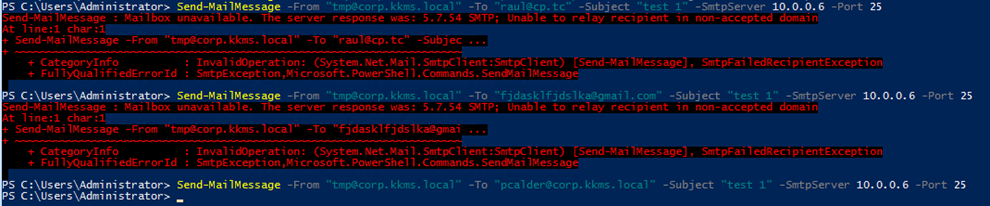
There are many ways to test this but we’re going to perform some manual testing.
We can see here that the server will not send emails to any random domain but can send emails to the domain within the network. There are some cases where there are compensating controls that prevent the email from being sent. To truly confirm if the test was successful is to speak with the client and confirm they received an email in their inbox.
Conclusion
There is so much more that can be done when you’re testing email systems but that is all that we will go over. I hope everyone is doing well and wish luck to those that made it to CPTC 9 Finals!